Well, in every scenario, how much ever you disagree, we do need a redundant connection to the internet, in case our primary connection fails. In this blog post I am going to talk about an interesting use case on a Palo Alto Firewall for redundant internet access using Policy based forwarding with two Virtual Routers.
To start with, let me explain you the use case we are trying to implement in this article. The following diagram shows that our Palo Alto firewall has two internet connections – primary internet connection on interface eth1/1 and secondary internet connection on interface eth1/4. Interfaces eth1/3 is connected to an internal host [in our case it is a Cisco router] which will be sourcing traffic to the internet.

The following steps explain the configuration starting from interface level configuration to implementing Policy Based Routing and then verifying:
We are using static IP addresses in our entire topology. The IP assignment is done in the following manner:
Palo Alto:
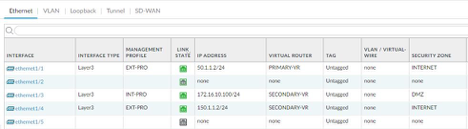
- Eth1/1: 50.1.1.2/24—–Primary Internet Connection
- Eth1/4: 150.1.1.2/24—Secondary Internet Connection
- Eth1/3: 172.16.10.100/24—-DMZ Router
Cisco Router:
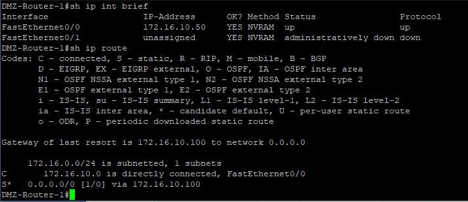
- F0/0: 172.16.10.50/24 with a default gateway of 172.16.10.100/24
Palo Alto Firewall interface configuration:
Cisco Router configuration [traffic source]:
The zone configuration on Palo Alto has been done as follows:
INTERNET: eth1/1 and eth1/4——these both are my internet connections.
DMZ: eth1/3——-here my Cisco Router is placed which will generate traffic.

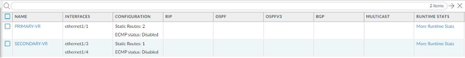
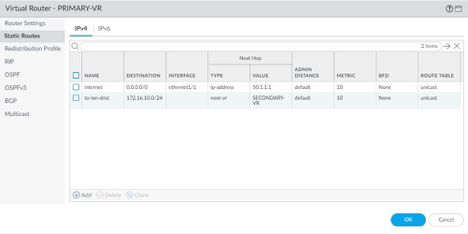
Virtual Router Configuration: In this scenario we have created two virtual routers one for primary connection which has eth1/1 and two static routes. One static route is for internet access i.e. the default route and one static route to reach the internal network for which the next hop is the other virtual router [Secondary-Router]. The other virtual router for secondary connection which houses the interfaces eth1/3 and eth1/4. It has one static default route for internet connectivity.
Primary VR Static Routes:
A simple security policy has been configured which permits all traffic from DMZ zone to INTERNET zone. Traffic is logged at the end of session.
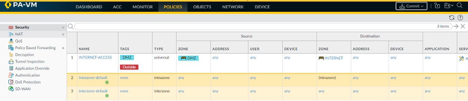
NAT policies have been configured for both internet facing interfaces. We have configured DIPP [Dynamic IP and Port] for traffic going to the internet.
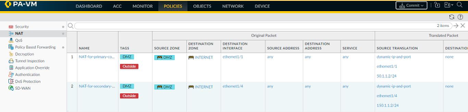
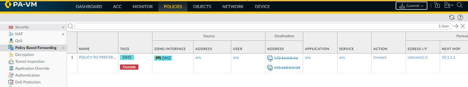
In the Policy section there is a tab for Policy Based Forwarding where we configure a policy which says that any traffic going to the internet has to be forwarded out via interface eth1/1. In the same policy we also have to consider that traffic destined to any private IP address which exists in the private network should be negated from being a part of this policy.
Verification:
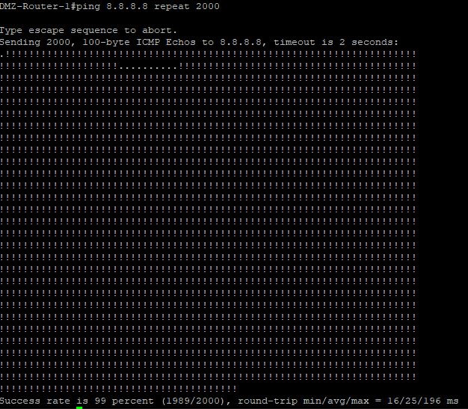
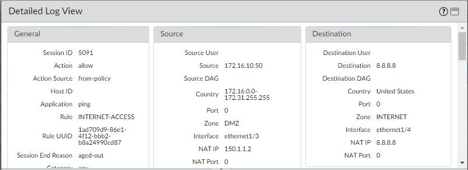
The following image shows the traffic generated from the Cisco router for 2000 ICMP request for destination IP of 8.8.8.8
Once traffic starts we shut down the primary link from the INTERNET router as shown.
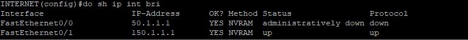
Traffic Forwarded via interface eth1/1 [primary interface]:

Traffic Forwarded via interface eth1/4 [secondary interface]:
To illustrate the same concept with hands-on configuration I have made a video as well which you can watch here: https://youtu.be/uXvrd0VrcqE
To know more about trainings offered for Palo Alto do check out our website or get in touch with us at enquiry@bluemap.co
Network Consultant and Trainer by profession with knowledge in multi-vendor environment ranging from routing and switching in Cisco and Juniper to firewalls from Cisco, Palo Alto, Juniper, CheckPoint and Fortigate to virtualization in Cisco UCS and design and deployment of Cisco Viptela SD-WAN solution. Successfully designed and deployed green field and grey field networks for various small to mid-scale organizations.
