BGP is a path vector routing protocol used to exchange routing information among routers in different Autonomous Systems [ASs]. BGP operates over TCP port 179. It is a reliable but slow routing protocol and it is also the routing protocol which runs the internet. JUNOS supports BGP version 4 [v4]. This version of BGP adds support for Classless Inter-domain Routing (CIDR), which eliminates the concept of network classes. BGP supports two types of neighbor relationship- ibgp [internal BGP peers- within same AS] and ebgp [external BGP peers – within different AS].
In this blog I will explain step by step configuration of BGP peers in Juniper vMX routers. To begin with, let us have a look at the topology:
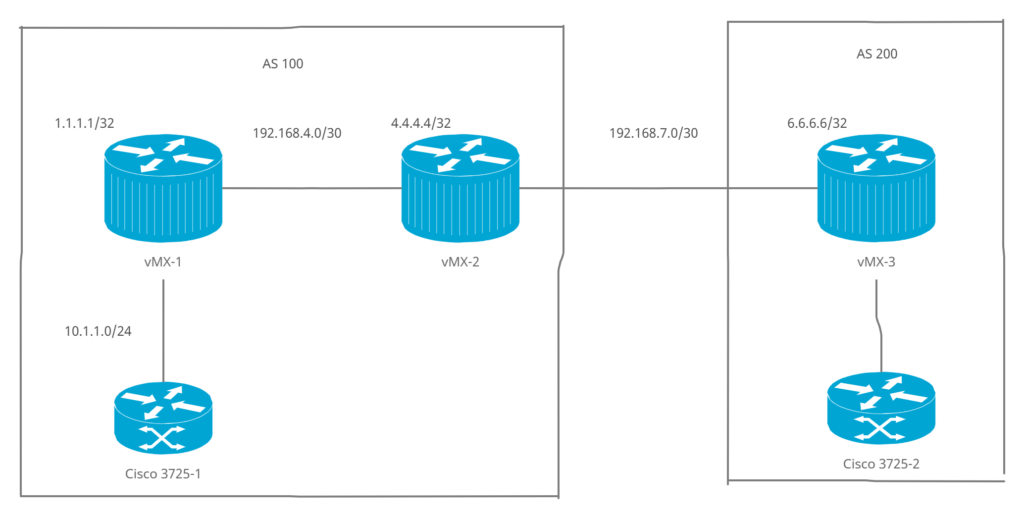
In this topology we have two Autonomous Systems – AS 100 and AS 200. In AS 100 we have vMX-1 and vMX-2 and in AS 200 we have vMX-3. Cisco routers 3725 acts as end host which we will be using to check connectivity at the end of the configuration.
Let us look at the steps involved to configure BGP in the above topology:
- IP Configuration on the interface: Assign IP addresses as displayed in the topology. You can copy paste the commands below in your router if you trying to create the same lab
vMX-1
set interfaces ge-0/0/2 unit 0 family inet address 10.1.1.1/24
set interfaces ge-0/0/3 unit 0 family inet address 192.168.4.1/30
set interfaces lo0 unit 0 family inet address 1.1.1.1/32
vMX-2
set interfaces ge-0/0/2 unit 0 family inet address 192.168.7.1/30
set interfaces ge-0/0/3 unit 0 family inet address 192.168.4.2/30
set interfaces lo0 unit 0 family inet address 4.4.4.4/32
vMX-3
set interfaces ge-0/0/0 unit 0 family inet address 10.1.3.1/24
set interfaces ge-0/0/2 unit 0 family inet address 192.168.7.2/30
set interfaces lo0 unit 0 family inet address 6.6.6.6/32
2. Autonomous System and Router-ID configuration: As shown in the topology the Autonomous System will be assigned as AS-100 for vMX-1 and vMX-2 and AS-200 for vMX-3. Router-ID is a logical parameter, you can either use the ones I have chosen or choose your own values
vMX-1
set routing-options router-id 1.1.1.1
set routing-options autonomous-system 100
vMX-2
set routing-options router-id 4.4.4.4
set routing-options autonomous-system 100
vMX-3
set routing-options router-id 6.6.6.6
set routing-options autonomous-system 200
3. eBGP peer configuration: eBGP peers are formed between routers which belong to two different Autonomous Systems. In our case eBGP peering will be done between vMX-2 of AS-100 with vMX-3 of AS-200. Follow the commands below to create eBGP peering. The address chosen for peering is the interface address for the routers.
vMX-2
set protocols bgp group BGP-Ext type external
set protocols bgp group BGP-Ext local-address 192.168.7.1
set protocols bgp group BGP-Ext peer-as 200
vMX-3
set protocols bgp group BGP-ext type external
set protocols bgp group BGP-ext local-address 192.168.7.2
set protocols bgp group BGP-ext peer-as 100
4. iBGP peer configuration: iBGP peers are formed between routers which belong to the same Autonomous System. In our case iBGP peering will be done between vMX-1 and vMX-2 in AS-100. In this case we choose the loopback IP addresses to establish iBGP peering, hence static routing is done on vMX routers to have connectivity with each other’s loopback interfaces
vMX-1
set protocols bgp group BGP-Internal type internal
set protocols bgp group BGP-Internal local-address 1.1.1.1
set protocols bgp group BGP-Internal peer-as 100
set routing-options static route 4.4.4.4/32 next-hop 192.168.4.2
vMX-2
set protocols bgp group BGP-Internal type internal
set protocols bgp group BGP-Internal local-address 4.4.4.4
set routing-options static route 1.1.1.1/32 next-hop 192.168.4.1
5. Routing Policy configuration: Till the above commands we have successfully established BGP connectivity between the routers. Now the next step is to advertise networks in BGP and to do the Next-Hop configuration for our iBGP peers. Speaking about routing policies the default policy for BGP is JUNOS says that import all routes and export nothing. To change this behavior and export our directly connected network into BGP we have to design an export route policy for BGP. Policy will be applied on the following routers for following purposes:
vMX-1: to advertise the connected the networks on vMX-1
set policy-options policy-statement Conn from protocol direct
set policy-options policy-statement Conn then accept
vMX-2: to configure Next-Hop-Self for vMX-1 and advertise networks in BGP. [Remember the next-hop-rule in BGP!!]
set policy-options policy-statement My-route from protocol direct
set policy-options policy-statement My-route from protocol static
set policy-options policy-statement My-route then accept
set policy-options policy-statement NHP term 1 from route-filter 1.1.1.1/32 exact
set policy-options policy-statement NHP term 1 then next-hop self
set policy-options policy-statement NHP term 2 from protocol bgp
set policy-options policy-statement NHP term 2 from protocol direct
set policy-options policy-statement NHP term 2 then accept
vMX-3: to advertise the connected the networks on vMX-3
set policy-options policy-statement My-Route from protocol direct
set policy-options policy-statement My-Route then accept
6. Applying routing policy in BGP: Once the policies have been designed it is time to apply the policy in the BGP configuration:
vMX-1
set protocols bgp group BGP-Internal neighbor 4.4.4.4 export Conn
vMX-2
set protocols bgp group BGP-Ext neighbor 192.168.7.2 export My-route
set protocols bgp group BGP-Internal neighbor 1.1.1.1 export NHP
vMX-3
set protocols bgp group BGP-ext neighbor 192.168.7.1 export My-Route
7. Verification: The result of the above configuration is shown below:
- vMX-1 BGP peers
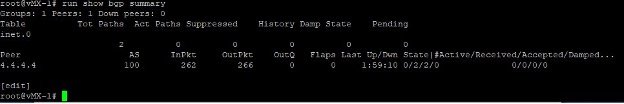
- vMX-2 BGP Peers

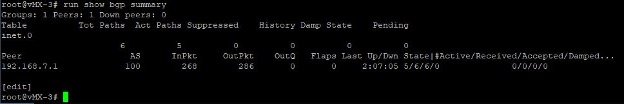
- vMX-3 BGP Peers
- vMX-3 BGP Routes

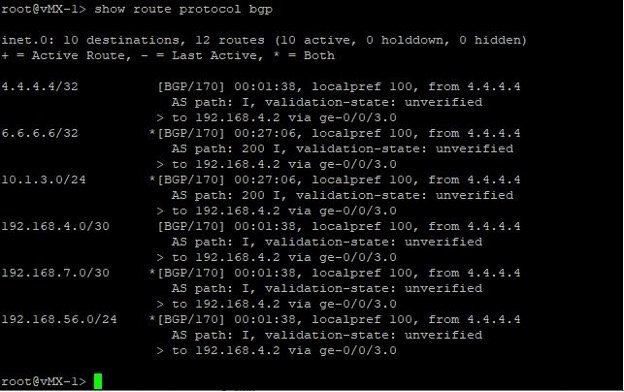
- vMX-1 BGP Routes
- Connectivity between Cisco 3725 acting as end devices

To know more about trainings offered for Juniper Network do check out our website or get in touch with us at enquiry@bluemap.co
Network Consultant and Trainer by profession with knowledge in multi-vendor environment ranging from routing and switching in Cisco and Juniper to firewalls from Cisco, Palo Alto, Juniper, CheckPoint and Fortigate to virtualization in Cisco UCS and design and deployment of Cisco Viptela SD-WAN solution. Successfully designed and deployed green field and grey field networks for various small to mid-scale organizations.

